On June 5 at 10:04pm UTC, a hacker stole 1,650,000 EGLD.
Congratulations to the Elrond team that worked non-stop and successfully recovered all the funds.
But where did the hacker steal the EGLD? And how?
It is time for full explanations
At 10pm, 3 accounts withdrew from 3 smart contracts huge amounts of EGLD that seemed to come from nowhere:
-450k EGLD on shard 0 (10:04pm)
https://explorer.elrond.com/transactions/39998ab5c929fa67e95d0c64081697fc4207235dbfeaaff10fb2704a6c7716b6
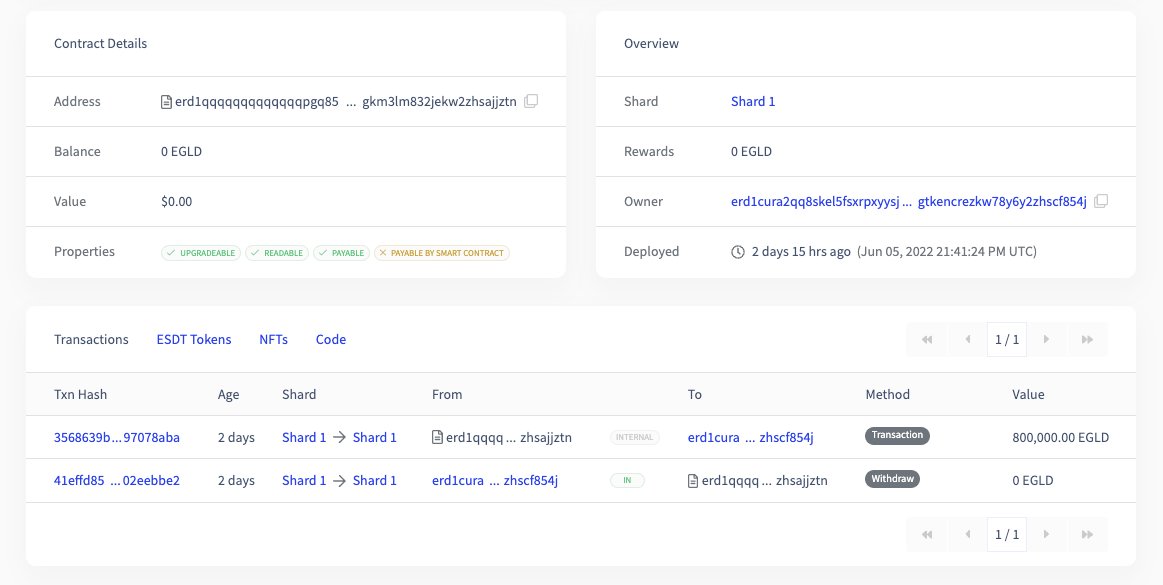
-800k EGLD on shard 1 (10:05pm)
https://explorer.elrond.com/transactions/41effd8536376f3a2edba7074c02776edae94bb5b464485ac414847202eebbe2
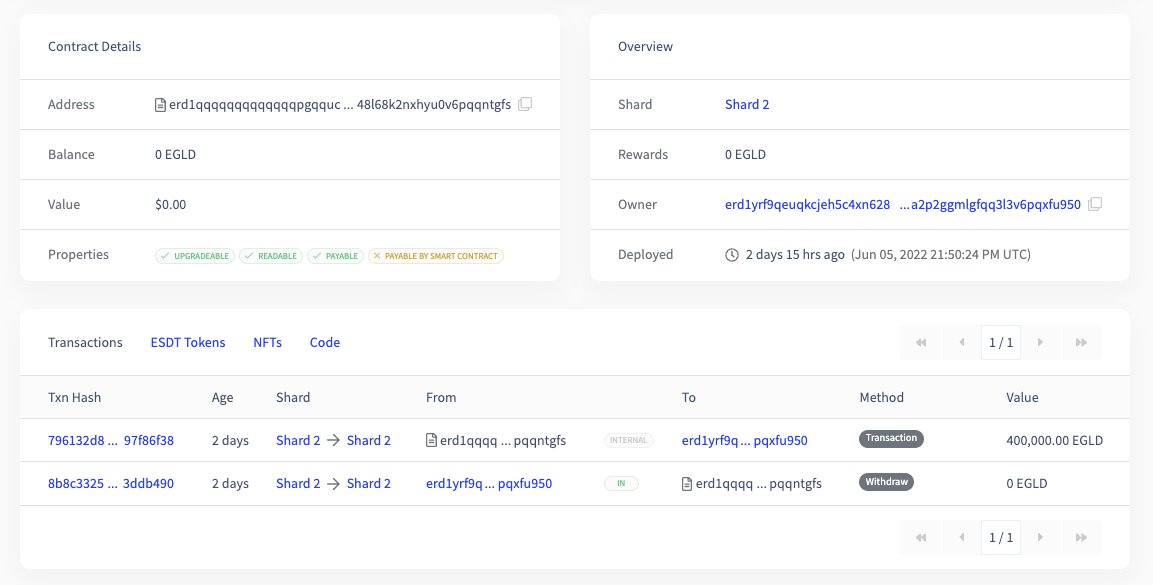
-400k EGLD on shard 2 (10:06pm)
https://explorer.elrond.com/transactions/8b8c332577e5b8bdd4e13450ea92b7c6b0ca15399f1f0bb38fc215cfc3ddb490

Let's focus on shard 1.
In the tx above, we see that the hacker received EGLD by calling the "withdraw" method of his SC (Smart Contract).
We downloaded the binary code of this SC from the explorer, and converted it to an easier-to-understand format (WAT format).


In this file, we searched the main methods of the SC.
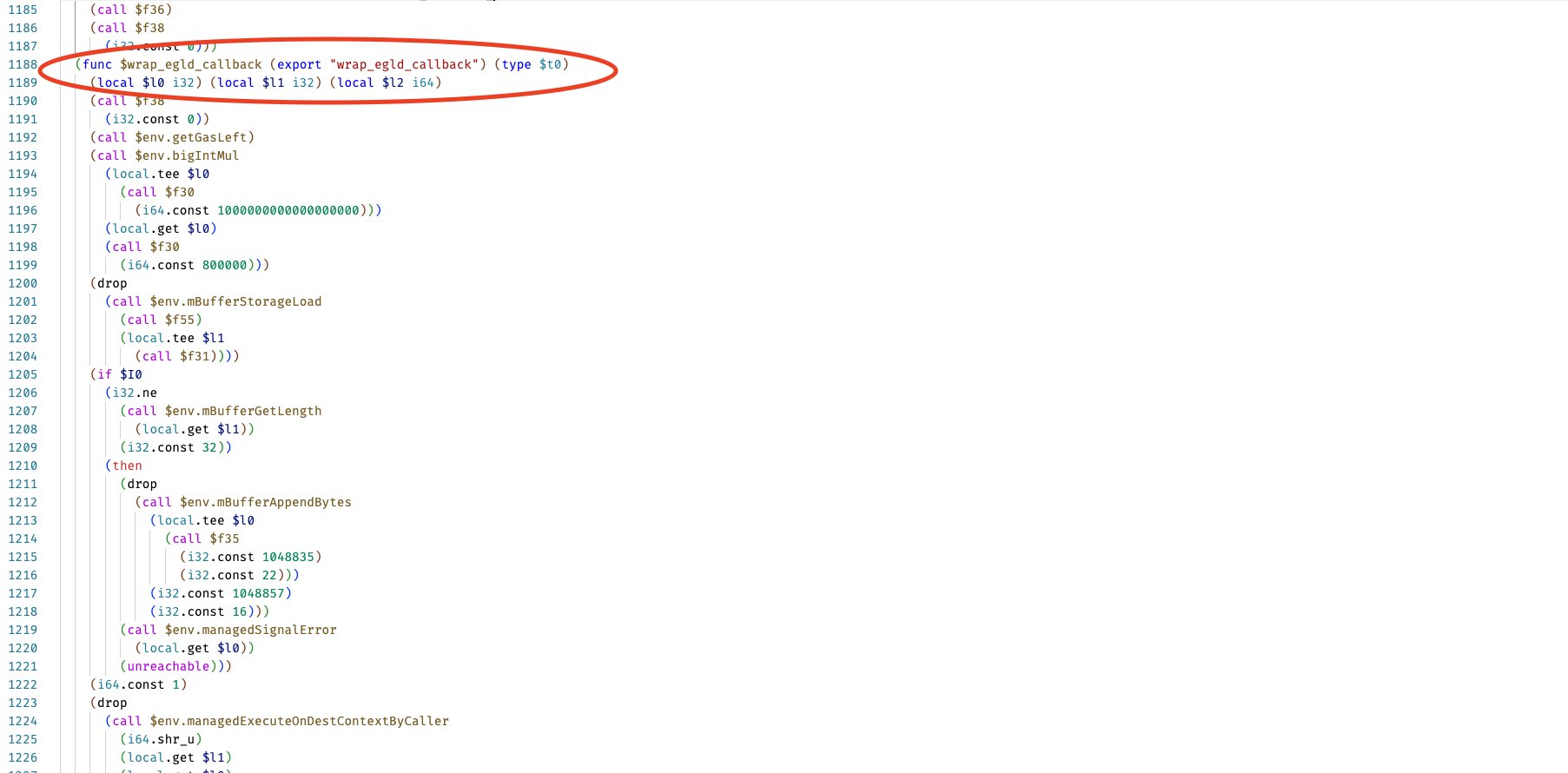
We found the "withdraw" method, but more importantly, a method called "wrap_egld_callback".
This suggests that the huge amount of stolen EGLD came from the WEGLD SC (in charge of wrapping/unwrapping EGLD).
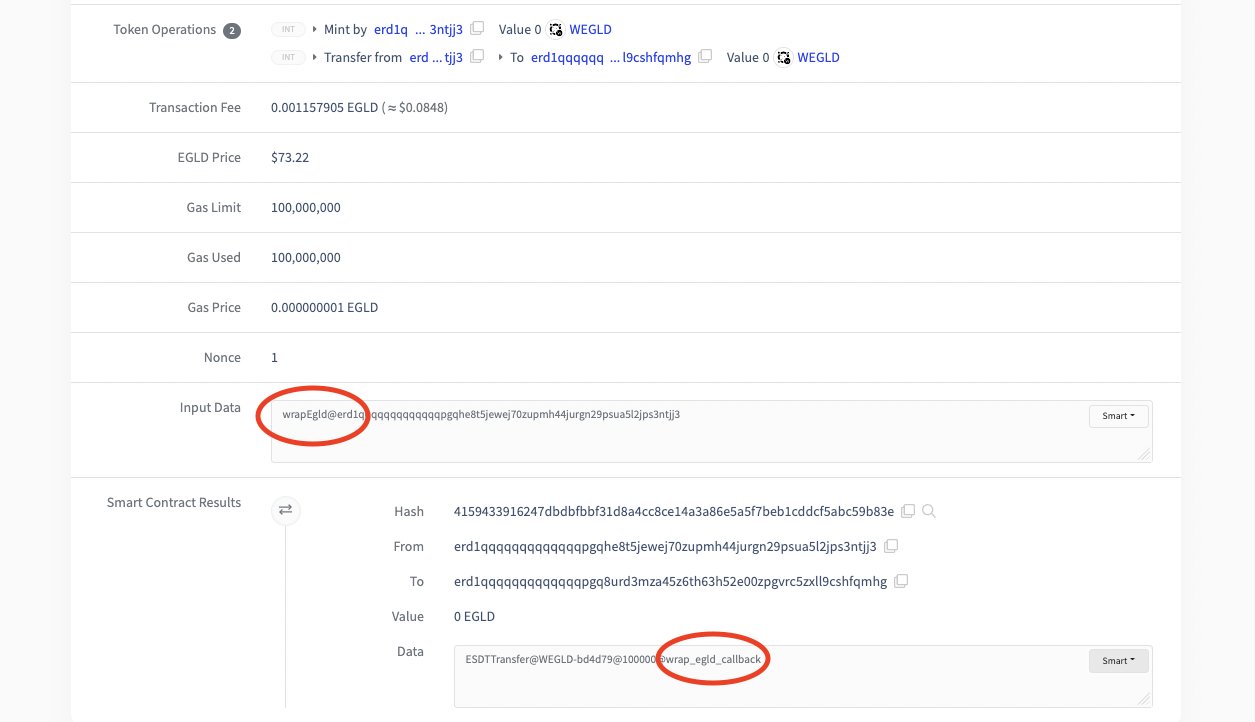
On the explorer, we hunted for suspicious txs going through WEGLD SC around 22pm.
We found one where WEGLD SC called the method of a new SC. And guess what... this method was named "wrap_egld_callback".
So we looked at the details of this tx.

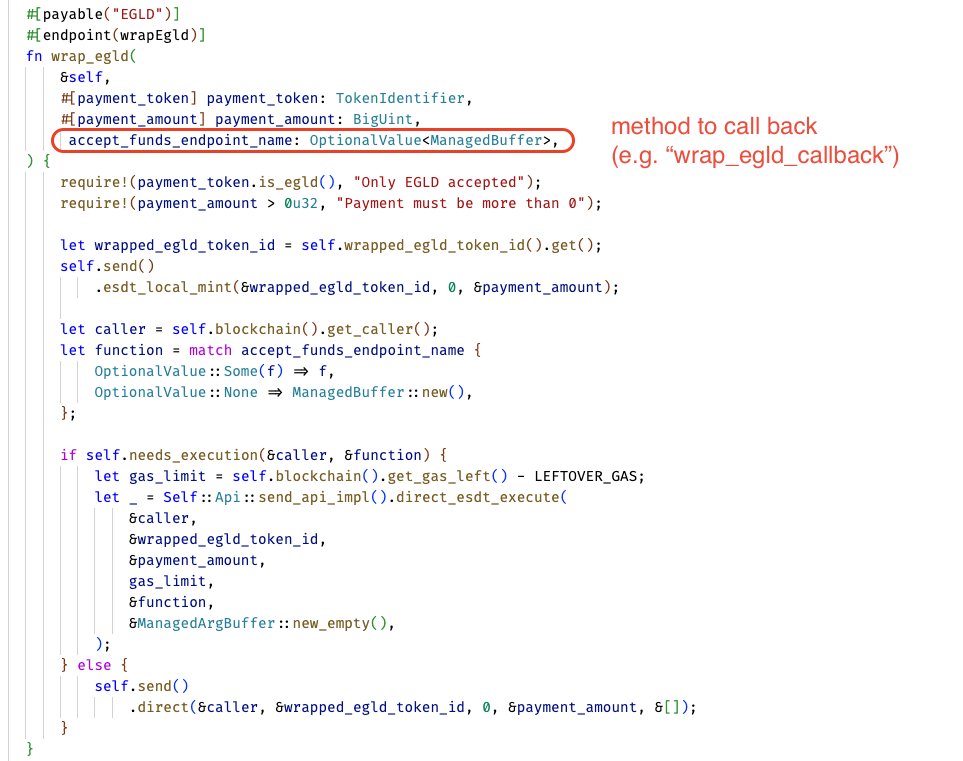
In this tx, the new SC sends a small amount of EGLD to the "wrapEgld" method of WEGLD SC. This method sends back WEGLD to the "wrap_egld_callback" method of the new SC.
Indeed, when calling "wrapEgld", we can specify the method WEGLD SC should call back.
We then found hard proofs that this new SC also belongs to the hacker:
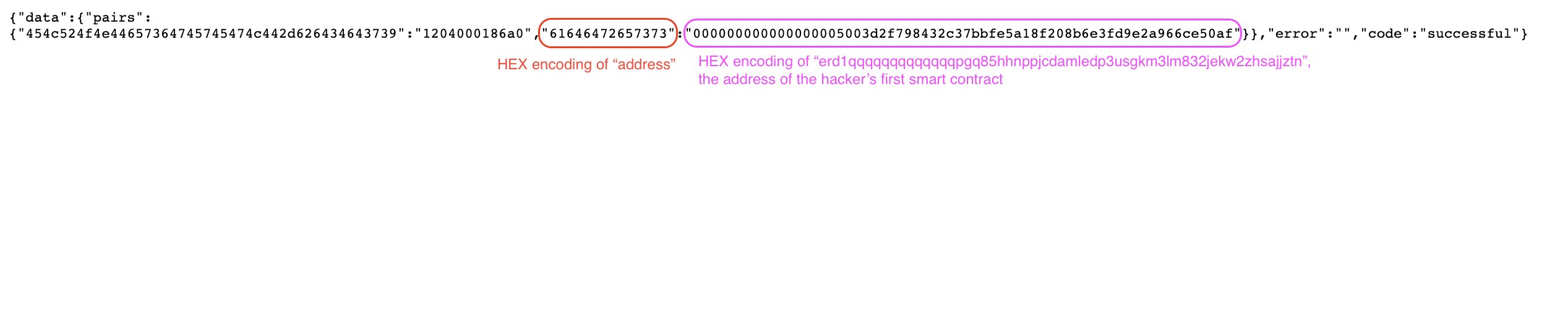
- In its storage, the new SC records the address of the first hacker's SC.
https://gateway.elrond.com/address/erd1qqqqqqqqqqqqqpgq8urd3mza45z6th63h52e00zpgvrc5zxll9cshfqmhg/keys
- The binary code of the new SC is exactly the same as that of the first SC.
To recap, the hacker deployed two contracts (SC A and SC B):
-At 10:01 PM, the hacker calls SC A. SC A calls WEGLD SC which wraps a few EGLD and calls back the “wrap_egld_callback” method of SC A.
-At 10:05 PM, he calls the “withdraw” method of SC B and receives 800k EGLD.
By inspecting the code of the “wrap_egld_callback” method, we discovered 2 interesting things (cf screenshot):
- The amount “800000" seems to define the amount of EGLD to transfer.
- The “managedExecuteOnDestContextByCaller” method seems to transfer the EGLD from WEGLD SC.

To validate these guesses, we made two repositories:
- one to reproduce the hack with hacker's binary code,
- one to reproduce the hack with our own Rust SC.
In both cases, we succeeded to make WEGLD SC send 800k EGLD to an address of our choice.
"managedExecuteOnDestContextByCaller" was the key ingredient of the hack.
As the name suggests, when WEGLD SC calls SC A, it allows SC A to execute a token transfer in the context of WEGLD SC, the caller.
This way, SC A was able to make WEGLD SC send 800k EGLD to SC B.
Congratulations if you arrived here: you've understood the hack in details!
If the EGLD withdrawn by the hacker seemed to come from nowhere, it is because they were transferred using “managedExecuteOnDestContextByCaller”, which the Explorer didn't display.
What we described on shard 1 happened in the exact same way on shards 0 and 2.
The hacker swapped the EGLD for USDC on Maiar and tried to bridge them to Ethereum.
To stop him, the Elrond team paused the necessary smart contracts and investigated.
Writing by Arda
Tweet Share

You can check if you are not dealing with a scam
Check now

 @elrondwiki.elrond
@elrondwiki.elrond